Protect your business-critical SAP landscape
SAP Security

Why it is so important to have SAP Security all of one piece
SAP application environments are a highly integrated part of an organization's value chain. They enable the handling of business processes and are an indispensable part of daily operations. In addition, they usually process and store sensitive and highly critical data.
The high flexibility of the SAP landscape and its used components also involves risks. The multitude of possible errors and vulnerabilities can cause operational, financial and reputational damage. This risk is all too often countered by isolated technical measures or corrections. In such a complex and integrated environment with its dynamics, influences and dependencies it is however important to manage SAP security in a risk-oriented way.
SAP Security all of one piece - PwC
This is a modal window.
Together with you our SAP security experts establish such a framework for your company. To ensure that the risk is appropriately addressed by technical and organisational measures. To assure that effectiveness is sustainable and not only limited to a certain point in time. To protect what is really important: The digital heart of your company.
What we do to help our clients
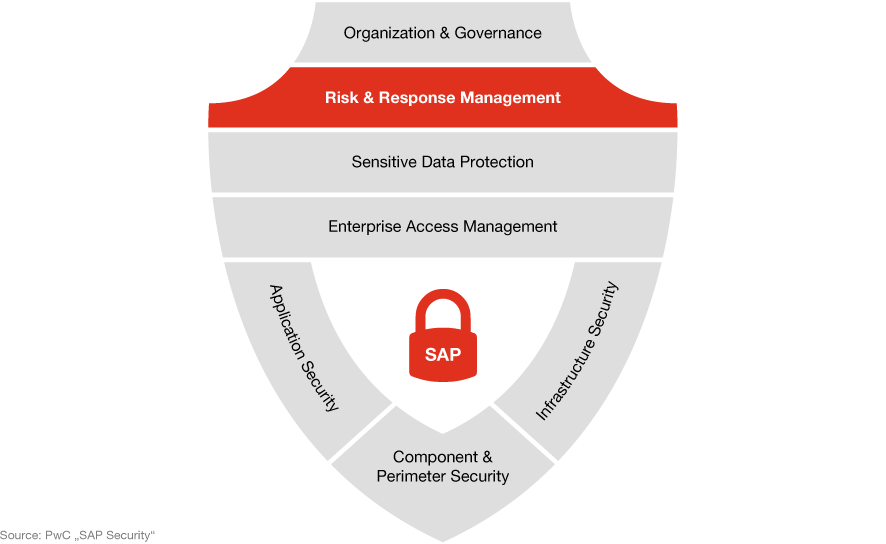
SAP security all in one
Our view on SAP security incorporates both technical and organizational dimensions. By aligning with established standards and regulatory requirements, we ensure that SAP security is seamlessly integrated into your security and risk management.
Organization und Governance
Bring your specialists together with clear roles and responsibilities!
Anchoring SAP security requires the establishment of an SAP security organization with defined roles and responsibilities. This enables the appropriate coordination of the distributed business, IT and SAP responsibilities in order to initiate and implement security measures in a targeted, efficient and sustainable manner.

Your journey to a secure SAP landscape
We are happy to master the challenge with you and accompany you from an initial evaluation of your SAP landscape to establishing a sustainable and controlled protection of your SAP landscape. Once you have made it down this path, you yourself will be able to transparently manage your organizations’ SAP security and react to new developments such as S/4, HANA, Fiori and cloud applications in a targeted and secure manner.

1st Stage: Evaluation of your SAP landscape and joint travel planning
We recommend a risk-oriented approach to raise the security level of your SAP landscape specifically and sustainably to the level you require. This is to ensure that resources are used cost-effectively and that security and business risks are minimized. For this purpose, we support you with a customized SAP security risk analysis and a resulting joint travel planning. In doing so, we always keep in mind that such a trip often requires various agreements and, depending on its characteristics, also a certain budget. Therefore, we support you with our experience in all necessary preparations.
2nd Stage: Remediation of organizational up to technical in-depth vulnerabilities
Depending on the risk, identified vulnerabilities in the SAP landscape should be specifically remedied. Our common path leads us past organizational, but also in-depth technical challenges. Together we design and implement targeted and sustainable security measures to master the path to a secure SAP landscape.
3rd Stage: Controlled SAP security and secure reaction to emerging challenges
After remedying identified vulnerabilities, frequently the question arises as to how a now secured SAP landscape can be maintained in the future. In order to avoid cost-intensive and subsequent clean-ups, an adequate and risk-oriented response should also be made to business and technical changes.
Together we will enable you as an organization to react to new developments − such as SAP S/4HANA − in a targeted manner.
SAP Security in your S/4HANA Transformation
Are you currently planning your S/4HANA transformation or are you already in the process? To avoid security vulnerabilities and resulting business risks during and after the implementation of S/4HANA, an early and appropriate implementation of security is essential. Explore now in this video.
SAP Security in your S/4HANA Transformation - PwC
This is a modal window.
Your advantages at a glance
SAP security based on established best practices and recommendations
In addition to our own good practices and recommendations, we take into account and orientate ourselves to common standards of SAP, the German-speaking SAP user group (DSAG) and the German Federal Office for Information Security (BSI). We support you with our accumulated expertise − and we do this tailor-made to your needs.
Combination of technical security expertise and understanding of your business
To ensure the security of SAP landscapes, it is necessary to handle SAP-specific and technical security matters. At the same time, it is necessary to understand your company and to design, coordinate and implement measures according to your needs. In Cyber Security & Privacy we offer you both: a strong technical and organizational understanding.
International Network
Especially in the environment of business applications such as SAP, international matters often have to be considered. At the same time, it is usually necessary to go into technical details of the various technologies used. We access the knowledge of our worldwide Cyber Security and Privacy expert network to provide you with the best possible support for your project.
“Quite often, SAP security activities are still limited to role design and access management or to technically-driven isolated measures. That is not enough: These measures are undoubtedly important, but without embedding them into a comprehensive framework, this is simply building steel doors into cardboard walls.”
Daniel Peisker,Senior Manager Cyber Security and Privacy at PwC GermanyContact us